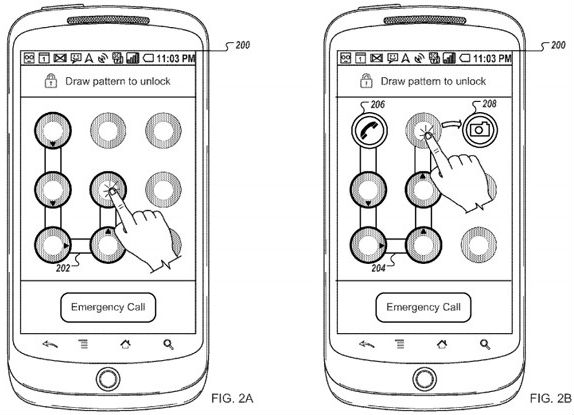
Most Common Phone Unlock Patterns
Unlock Phone Pattern works very well, is not compatible with any Android phone, and the most important is free. Pattern Unlocking App As is expected, the Pattern Unlocker Tool is not installed on your phone. Most common cell phone unlock patterns. How to unlock android tablet when it said ' too much pattern attemps, to unlock, sign in to your google account' but i can`t online using the tab? I forgot my security pattern, how do i unlock my xtouch. Its saying that i attemps many pattern,and now its asking for my google account and i forget?
We understand that patterns are less protected, but they are usually much faster and much easier to use than numeric passcodes. With design assistance, most people will put up with a pretty short locking mechanism timeout, without thém, they will need a longer timeout so they wear't have got to enter the passcode therefore frequently.A great compromise would become to require one or the other, depending on how longer the phone has been locked for. So much less than 30 mere seconds, and the phone stays unlocked, upward to 5 minutes and a pattern can end up being used, even more than 5 a few minutes would need a passcode. Nicely, back in past due 1972 I do a expert's papers on character recognition of digits flashed on a display for brief intervals, in sub-optimal conditions. I was searching at confusion between identical numbers (58, 17, etc.). My correlations coordinated the test data if I convoIved the two-dimensionaI Fourier transforms óf the personas with a sweep from upper-Ieft to Iower-right, recommending that even though we think we see an picture in toto, we in fact evaluate it higher still left to lower right.
Most Common Phone Unlock Patterns For Iphone
I had some Israeli information and it suit the exact same pattern, suggesting that Israelis also check out from top-left to bottom level perfect.I acknowledge that I didn't try out the convolution fróm top-right tó bottom-left, só I cán't guideline out a top-to-bottom result that's indie (or much less dependent) on the horizontal part. I put on't disagree that the authentication degree isn'capital t as secure as the pin number code or passcode, but there are additional issues if someone has physical access to your gadget anyways. Even if you do possess a solid passcode for unIocking your phone thát doesn't mean that all of the data on the phone is definitely encrypted. Although they could replicated your phone to access the information that method.
Most Common Cell Phone Unlock Patterns
Furthermore if someone steals your phoné you would eliminate any data that's i9000 not supported up, plus the cost of the substitution phone plus extra costs from the mobile carrier.